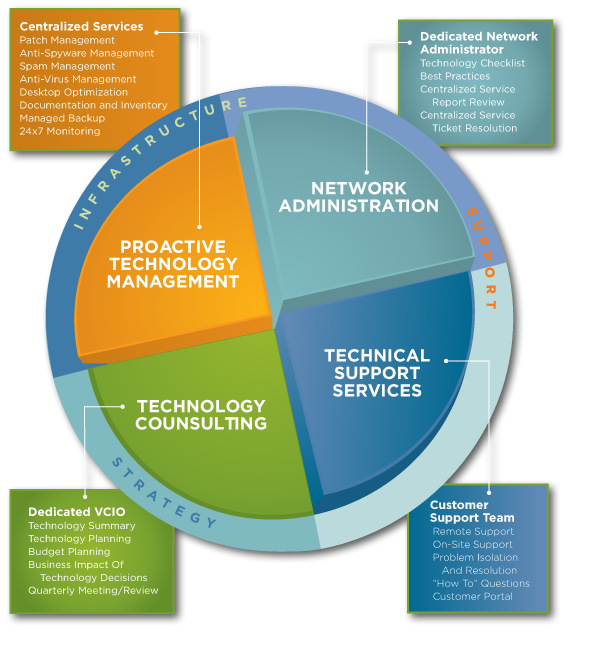
We thrive in vast ranges of solutions such as network security design, integration, operation, maintenance and modernization of complex data, voice and multimedia networks.
Working closely with customers, we ensure their network infrastructures are secure, efficient, scalable and cost-effective.